What Best Describes an Insider Threat Choose All That Apply
Lock your computer screen and mobile devices every time you step away. Select all that apply Which of the countermeasures can you.
Applied Sciences Free Full Text A Review Of Insider Threat Detection Classification Machine Learning Techniques Datasets Open Challenges And Recommendations Html
Insider threat indicators are clues that could help you stop an insider attack before it becomes a data breach.
. Which term best describes Mr. Strengthening the agency and the ability of its employees to thwart insider threats and adversarial intelligence collection activities in order to protect vital agency assets. Start studying the Insider Threat Awareness flashcards containing study terms like Sharing details of your personal and professional lives or life online makes you _____ adversaries Which of these activities must be reported.
Select all that apply. Insider threat Hacktivist Organized crime Insider threat 9 Which of the following terms best describes a type of threat actor that engages. WPA-2 is the best available encryption security for the system.
True 12 Physical threats to companies include. Contractors must report the following to the insider threat program. Which term best describes Mr.
Instead of attempting to manage the human side of risk Insider Risk Management looks at the data that could be breached and implements monitoring and protections that make it difficult for any threat actor. At many companies there is a distinct pattern to user logins that repeats day after day. Increasing Insider Threat Awareness.
What type of insider threat would Joe be considered. Keep your desk free of any proprietary or confidential information. Human behaviors are the primary indicators of potential insider threats.
DIY 48 Catio Plan. When an insider becomes a threat it can have far-reaching consequences on both an organization and national security. Terrorism is deliberate Terrorism is used to cause fear Terrorism can be used to intimidate governments Terrorism can be used in an effort to achieve political or ideological goals.
Memorize flashcards and build a practice test to quiz yourself before your exam. Your lucky kitty will have a sturdy yet sleek space to nap play and exercise. The threat may involve fraud theft of confidential or commercially.
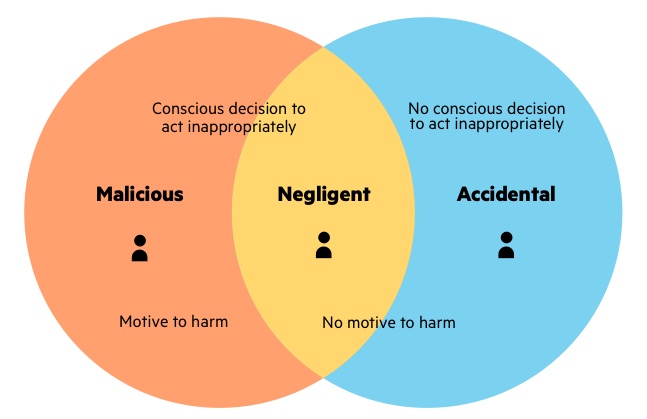
A malicious insider is one that misuses data for the purpose of harming the organization intentionally. Efforts to obtain unauthorized access to classified or proprietary information. Train your team to recognize different abnormal behaviors and use Varonis to detect activity that indicates a potential insider threat.
Insider Risk on the other hand is a data-focused perspective. Which of the following best describes the result of this command query. Select all that apply IPsec MPLS PAP Kerberos CHAP IPsec Kerberos CHAP A REPLAY ATTACK is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed.
Recruitment information collection information transmittal and general suspicious behavior. Allowing large amounts of data to be accessed Presenting new security. Select all that apply.
Contractors must report which of these to the insider threat program select all that apply. An insider threat is any employee vendor executive contractor or other person who works directly with an organization. An insider threat does not have to be a present employee or stakeholder but can also be a former employee board.
Keep in mind that not all insider threats exhibit all of these behaviors and. Insider threat What manipulation technique is used when an FIE operative develops a sexual relationship with an insider to draw in the target. Choose two Always be considerate such as holding the door open for people even if you dont know them.
Contact with foreign diplomatic offices for other than official duties. Which of the following is the best choice in choosing security guard for a physical access control. Choose all that apply A.
Select all that apply. Select ALL that apply. Contact with foreign.
The threat than an insider will access information without a need to know. 3 Select the response below that BEST describes your level of experience with coordinating and providing tailored insider threat INTH andor counterintelligence CI services that include. Question and answer.
Insider threat management attempts to identify potential threat actors and mitigate the risk that they pose. An insider threat is anyone with authorized access to the information or things an organization values most and who uses that access either wittingly or unwittingly to inflict harm to the organization or national security. Threat can include damage thought espionage or terrorism.
Keep an eye out for the following suspicious occurrences and youll have a far better chance of thwarting a malicious insider threat even if its disguised as an unintentional act. Select ALL that apply. Choose all that apply A.
Insider Threat Awareness The Insider Threat and Its Indicators Page 2 Indicators Indicators of a potential insider threat can be broken into four categories--indicators of. Any contact by cleared employees with known or suspected intelligence officers from any country. Pin On Cage Project 1 The first leg will be left as it is to be used as a door later 2 The second leg will support half the bottom platform cut a 1 13 piece but dont forget the 14 less for the fitting and then take 14 off the longer 3 23 piece.
Which situations should be reported. An insider threat is most simply defined as a security threat that originates from within the organization being attacked or targeted often an employee or officer of an organization or enterprise. __________ is a conversation technique used to discreetly gather information that is not readily available and do so without raising suspicion.
Select all that apply. Honey pot Which situations should be reported. Technological advances impact the insider threat by ______________.
A Definition of Insider Threat. An insider threat is a threat to an organization that comes from negligent or malicious insiders such as employees former employees contractors third-party vendors or business partners who have inside information about cybersecurity practices sensitive data and computer systems. Identify two best practices for physical security awareness.
Like a user accessing data they have never. Physical security has a different set of threats vulnerabilities and risks when compared to other security issues we address in this series. Threat can include unauthorized disclosure of national security information or thought the loss or degradation of department resources or capabilities.

Malicious Insiders Types Indicators Common Techniques Ekran System

What Is An Insider Threat Malicious Insider Attack Examples Imperva

Malicious Insiders Types Indicators Common Techniques Ekran System
Comments
Post a Comment